I originally found this on a Netherlands forum and translated it. I wanted VPN on a Synology NAS to be much more secure so followed this great guide and it works great!!
Credit to = https://www.synology-forum.nl/vpn-server/beter-beveiligde-openvpn/
Translated here =
The main reason for writing this manual was that Synology does not make the OpenVPN Server package as secure as possible. It is namely sensitive to a
M an
I n
T he
M iddle attack because there is no verification of certificates from both the Server and the Client (s).
Authorization therefore only takes place by username / password. To counteract the
MITM risk, I have changed a number of things in the OpenVPN Server package. However, the change does not only concern the MITM attack.It is written in a “click this click that” way to keep following the steps as simple as possible. It is not very difficult to implement, but you have to sit down for it. It describes the steps to build a VPN tunnel from an Android phone, but it also works with other clients such as Windows, Apple, Linux, etc.
It works in such a way that a relatively secure connection is created.
At least 90% comes from the OpenVPN documentation and the OpenVPN manual 2.3 .
The OpenVPN Server (Package VPN Server) has a “hidden” option to use its own configuration, which is used in this manual. This option is not officially supported by Synology.
This also ensures that the configuration is not overwritten by an update or restart. From DSM 5.0 to the present I can say that it hasn’t happened to me yet. Nevertheless it may happen that we do, we do not know what changes Synology will make with future updates.
The own configuration option means that you can no longer make any settings in the OpenVPN Server screen and at the bottom you get the message in blue: OpenVPN configuration is adjusted The adjustment is arranged in such a way that the certificates generated in this manual are only for OpenVPN being used. Purchased / free / Let`s encrypt / etc. SSL certificates that are imported into DSM will continue to function even if they have already been imported.
In short, OpenVPN is separated from the rest of the system in this regard, as it should be.
After performing the steps, the VPN connection to the NAS, the devices in the network where the NAS / VPN Server is located, can be accessed via their IP.
Tested:
Every DS model.
DSM 5 and higher.
Clients:
Android 4 to 9
Android 6 The energy saving function may need to be switched off for the VPN App, see here and here . This is an Android issue and is separate from this manual.
Samsung 6.x VPN is reported not to work unless the VPN app is excempted from Powersave features
OpenVPN Connect for Android up to and including version 3.0.5
OpenVPN for Android (Arne Schwabe) up to and including version 0.7.8 (recommended on Android 5.1 and higher)
Any DS model.
Windows 7 to 10
OpenVPN client for Windows :
Windows installer (NSIS, from Vista) – openvpn-install-2.4.7-I607.exe
Windows XP is no longer supported.
pfSense (FreeBSD) 2.2 and higher
Debian 8.7 jessie and higher
Ubuntu 14.04 LTS and higher
Linux Mint 18 and higher
MX Linux 18 and higher
System76 Pop! _OS 18.04
Puppy Linux (XenialPup and higher (UbuntuLTS16.04))
OpenATV 5.1 and higher
OpenPLi 5 and higher
The goal is:
User / Password – Standard
Client identification by certificate (server identifying client) – Non-standard
Server identification by certificate (client identifying server) – Non-standard
Diffie Hellman Perfect Forward Secrecy with 4096 bits encryption – Standard 1024/3072 bits, version dependent
Stronger encryption
tls-auth – Non-standard – Offers protection against DoS attacks, UDP port flooding / scanning and more
Added value:
Own root Certificate Authority exclusively for OpenVPN
Client identification through certificate
Server identification through certificate
DH Perfect Forward Secrecy 4096 bits
Stronger encryption for control and data channel
tls-auth (also called HMAC firewall)
What do we need:
Windows machine with XCA on it, download is here . Also available for Linux and MAC.
VPN Server to be found in the Package Center
WinSCP
PuTTY
How to use WinSCP and PuTTY
Android phone
Official client App OpenVPN Connect
Step 1
cert, key and DH files
We start by generating the certificates, key`s and the Diffie Hellman file.
We will do this with XCA.
With XCA we can set up a CA (Certificate Authority), generate and sign Server and client certificates / keys.
The certificates with associated private keys are stored in a database and then we export them for use on the server and client (s).
To save the files that we are going to create, we will create a folder named Database.
1. Create a
database.
Start XCA and click on File -> New DataBase.
Save the database with the name OpenVPN and enter a password.
We also need this password to be able to open the database again later if we still need it.
* Edit:
Templates added. First
download the XCA templates for this manual.
Then import it on the Templates tab in XCA before following the following steps.
*
What if we want to generate more certificates for the benefit of multiple clients?
For that we will have to repeat the steps to generate and export client certificates and client keys.
These are steps 4. 8. 9.
For each client, enter the exact username that he / she has in DSM, in the commonName and Internal name fields , commonName is a requirementInternal name is for recognisability.
Each of the clients must also be a user in DSM and must have the rights to use VPN, you set this in the VPN Server under Rights.
2.
Generate CA.
Click on the Certificates -> New Certificate tab.
On the Source tab we select:
Create a self signed certificate with the serial 1
Signature algorithm SHA 256
CA
Click Apply all.
On the Subject tab, we enter CA for Internal name and commonName.
Click Generate a new key.
The following screen: CA, RSA, 4096 bit and click Create.
On the Extensions tab we set the Time range to 10 Years and click Apply.
On the Key usage tab we select on the left:
Digital Signature
Key Encipherment
Data Encipherment
Key Agreement
Certificate Sign
CRL Sign
On the right we do not select anything.
On the Netscape tab, we only remove the comment and click on Ok.
Now we have generated a CA with which we can sign the server and client (s) certificates.
This CA now appears under the Certificates tab.
3.
Generate server certificate.
On the Certificates -> New certificate tab.
On the Source tab we select:
Use this Certificate for signing CA
Signature algorithm SHA 256
SERVERCERT
Click Apply all.
On the Subject tab, we fill in Internal name and commonName Server.
Click Generate a new key.
The following screen: Server, RSA, 4096 bit and click Create.
On the Extensions tab we set the Time range to 5 Years and click Apply.
On the Key usage tab we select on the left:
Digital Signature
Key Encipherment
On the right we only select TLS Web Server Authentication.
On the Netscape tab, we de-select everything and remove the comment and click OK.
Now we have generated a Server certificate that will be placed on the OpenVPN Server.
On the certificates tab, click on the arrow next to the CA so that it appears.
4.
Generate client certificate. (Repeat for multiple clients)
On the Certificates tab -> New certificate.
On the Source tab we select:
Use this Certificate for signing CA
Signature algorithm SHA 256
CLIENTCERT
Click Apply all.
On the Subject tab, we enter the Internal name and the CommonName client. (For multiple clients, enter the username)
Click Generate a new key.
The following screen: username, RSA, 4096 bit and click Create.
On the Extensions tab we set the Time range to 5 Years and click Apply.
On the Key usage tab we select on the left:
Digital Signature
Key Agreement
On the right we only select TLS Web Client Authentication.
On the Netscape tab, we deselect everything and remove the comment and click OK.
Now we have generated a client certificate that will be placed on the OpenVPN client.
5.
Export CA.
On the Certificates tab, select CA and click Export.
Choose the Database folder that we created earlier.
Export Format PEM and click Ok.
6.
Export server certificate.
On the Certificates tab, select Server and click Export.
Choose the Database folder that we created earlier.
Export Format PEM and click Ok.
7.
Export server private key.
On the Private Keys tab, select Server and click Export.
Choose the Database folder that we created earlier.
Export Format PEM and click Ok.
8.
Export client certificate. (Repeat for each client)
On the Certificates tab, select client and click Export.
Choose the Database folder that we created earlier.
Export Format PEM and click Ok.
9.
Export client private key. (Repeat for each client)
On the Private Keys tab select client and click Export.
Choose the Database folder that we created earlier.
Export Format PEM and click Ok.
10.
Generate Diffie Hellman parameters.
Click on Tools -> Generate DH parameter (XCA version older than 1.3.2 under File)
DH parameter bits 4096 and click on Ok.
This will take a while, let it go, have a drink and wait …..
Have a drink …..
…..
….
…
..
Choose the Database folder that we created earlier and click Ok.
If it went well, we now have in the database directory the following files:
Openvpn.xdb
ca.crt
client.crt (or <username> .crt)
client.pem (or <username> .pem)
dh4096.pem
server.crt
Server.pem
Rename client.pem to client.key (or <username> .key)
Rename Server.pem to Server.key
Step 2
Install and set up the VPN Server.
In the Package Center we find the VPN Server under Utilities.
After it has been installed and started, we will do some settings.
Open Main Menu and click on VPN Server.
In the screen we now see the overview.
Under Rights we now first distribute the rights.
Under PPTP and L2TP we do not give anyone any rights unless you use it too.
Click Apply.
Go to OpenVPN, left in the menu.
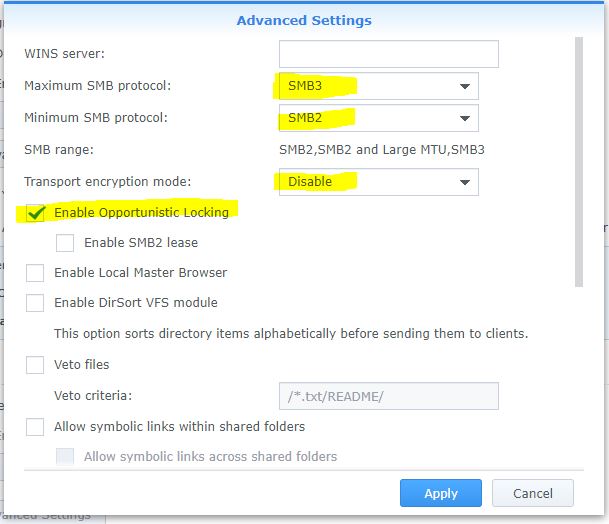
In this screen we check:
Enable OpenVPN server Enable
compression on the VPN link
Clients give access to the LAN server
Dynamic IP address: 192.168.160.1
Click Apply.
The rest can stay that way.
Now stop the VPN Server in the Package Center.
******************************************************** ******************************************************** ************
Avoid IP / route conflicts.
We are dealing with three subnets:
1. The network where the VPN Server / DS is located (local network)
2. The Dynamic IP address of the VPN (tunnel network)
3. The remote network from which you connect to a VPN client (Telephone, Laptop, Tablet, etc.)
These must be separate subnets.
Because you hardly ever have any influence on the IP address that your client gets from the remote network, it is therefore wise to choose the network where the VPN Server / DS is located as well as Dynamic IP address somewhere in the middle.
For the local network eg: 192.168.150.xxx (instead of the standard subnets that router manufacturers use, see list below )
For the Dynamic IP address, for example: 192.168.160.1
The chance that the remote network from which you connect with the client to the VPN Server / DS, uses the same subnet, becomes smaller.
Useful private subnets are:
Class A: 10.0.0.0 – 10.255.255.255 (10.0.0.0/8)
Class B: 172.16.0.0 – 172.31.255.255 (172.16.0.0/12)
Class C: 192.168.0.0 – 192.168.255.255 ( 192.168.0.0/16)
The list below are standard subnets that manufacturers use, ie as far as I have been able to find.
You do not want to use it as a local network or Dynamic IP address.
10.0.0
10.0.1
10.1.1
10.1.10
10.2.0
10.8.0
10.10.1
10.90.90
10.100.1
10.255.255
169.254 # APIPA #
172.16.0
172.16.16
172.16.42
172.16.68
172.19.3
172.20.10 # IPhone built-in hotspot #
192.168.0
192.168.1
192.168.2
192.168.3
192.168.4
192.168.5
192.168.6
192.168.7
192.168.8
192.168.9
192.168.10
192.168.11
192.168.13
192.168.15
192.168.16
192.168.18
192.168.20
192.168.29
192.168.30
192.168.31
192.168.33
192.168.39
192.168.40
192.168.42 # Android USB tethering #
192.168.43 # Android built-in hotspot #
192.168.50
192.168.55
192.168.61
192.168.62
192.168.65
192.168.77
192.168.80
192.168.85
192.168.88
192.168.98
192.168.99
192.168.100
192.168.101
192.168.102
192.168.111
192.168.123
192.168.126
192.168.129
192.168.137 # Windows Phone built-in hotspot #
192.168.168
192.168.178
192.168.190
192.168.199
192.168.200
192.168.220
192.168.223
192.168.229
192.168.240
192.168.245
192.168.251
192.168.252
192.168.254
200.200.200
******************************************************** ******************************************************** ************
In the router, UDP port 1194 must be forwarded to the NAS.
Register on the forum for the router and possibly the firewall because this is specific to everyone.
If you do not yet use “Automatic blocking”, it is now time for that.
Control panel -> Security -> Automatic blocking
Each DS model has a maximum number of VPN users that you will find in the specifications of your model.
Now we leave the VPN Server and go “under the hood”.
Step 3
Adjust the VPN Server.
Now we are going to put the certificates and keys that we created in Step 1 in the right place.
We are also going to make a ta.key that is needed on the server and client for extra protection.
First a summary of what that reads:
/ usr / synonym / etc / packages / VPNCenter / VPNcerts
ca.crt
server.crt
server.key
dh4096.pem
ta.key
/ usr / synonym / etc / packages / VPNCenter / openvpn
Here you will find openvpn.conf.user.
1. WinSCP
Navigate to: / usr / syno / etc / packages / VPNCenter
Create a new folder named:
VPNcerts
Copy the newly created CA.crt, Server.crt, Server.key and dh4096.pem to the folder.
Permissions as follows:
0400 for CA.crt, Server.crt, Server.key
0400 for dh4096.pem We set
permissions in WinSCP with right-mouse-button-> properties on the relevant file.
2. PuTTY (Terminal is also present in WinSCP. See menu Commands -> Open Terminal)
SSH to the NAS and type the following one after the other:
cd /usr/syno/etc/packages/VPNCenter/VPNcerts
Depending on the DS model, there may not be an Apparmor present.
To generate the ta.key we must first stop Apparmor:
/usr/syno/etc.defaults/rc.sysv/apparmor.sh stop
generate ta.key:
openvpn --genkey --secret ta.keyThere is now a ta.key in the VPNcerts folder.
Permissions (with WinSCP) as follows:
0400 for ta.key
The ta.key will also be needed in the OpenVPN Connect App.
Handy if you now copy it to the Database folder with WinSCP.
Restart Apparmor:
/usr/syno/etc.defaults/rc.sysv/apparmor.sh start
And finally:
exit
3. WinSP
Navigate to / usr / syno / etc / packages / VPNCenter / openvpn
Download the openvpn-server.zip configuration file at the bottom of this post, unpack it and follow the instructions in openvpn.conf.user. You can open / edit the file with a double click in WinSCP.
Place openvpn.conf.user in the above folder with rights 0400.
If everything is done correctly, we are ready on the VPN Server and you can now start it via the Package Center.
If you get a message in VPN Server to check the configuration file, stop the VPN Server.
Use WinSCP to navigate to / var / log and open openvpn.log to see what the message is.
Step 4
Put your SD card from the phone in the PC and create a folder with the name VPNcerts.
Copy the files that we created in the first step to this folder.
CA.crt, client.crt and client.key. (or CA.crt, username.crt and username.key) Also
copy the ta.key from step 3 here.
Download the openvpn-client.zip configuration file at the bottom of this post, extract it and follow the instructions in openvpn.ovpn You can open / edit the file with a double click in WinSCP.
Place openvpn.ovpn also in the VPNcerts folder and then you put the sd card back in the phone.
Download OpenVPN Connect from OpenVPN in the Play store and install it.
Open the App and import Profile from SD card.
Navigate to the VPNcerts folder on the sd card where we have stored the CA, crt, key, ta and ovpn.
Select the openvpn.ovpn profile and enter your username and password.
The rest of the files are automatically imported with the openvpn.ovpn profile.
This means that if you edit the profile, you will have to import it again.
Once the connection works you can delete the VPNcerts folder for security reasons.
There is also an option to save CA.crt, client.crt, client.key and ta.key in the ovpn profile.
Then you only have to hand over one file to a user.
This option, called “Inline file support” can be found here .
After configuring all of this it all works great and I can connect more securely using OpenVPN on a Synology NAS.